Five simple ways to increase your privacy that will allow you to take away the pleasure of government and corporations violating your privacy, while with minimal effort.
Best email services for privacy
In the first part of the series, let’s look at email providers. This article will partially introduce you to the important aspects that you should pay attention to when choosing this provider, and after this synopsis, it will offer you a choice of several different provider options.
Why should this bother you? And here’s why.
As far as basic security is concerned, email is usually the Foundation of people’s lives on the Internet. For many websites and account providers, having an email address is the very basis for registration. As a focal point for someone’s existence on the Internet, even if they get relatively minimal usage at the moment compared to social networks and the like, they still leave very large footprints and metadata that governments and corporations can, and will only use against you. And all (as they claim), for your own good.
Most people these days use Gmail accounts via Google. Unfortunately, it has been proven that Gmail reads and scans all outgoing and incoming content for metadata, which will then be used to create a profile about you, so that it can then be used for targeting, advertising, or linking you to a specific demographic.
It knows everything about your location, what you like and where you went from the very first day you started using it. As they often say, if the product is free, then the product is you. And, as with tech giants like Google, they offer you a free email account for nothing at all. There are consequences if you agree to such providers that will track you at every step you take while navigating the network.
Fortunately, there are many ways to get around this, even for free. There are many email providers that cost a penny a day to operate, and some are even free with paid versions if you need advanced functionality, storage, or other similar services.
And then the question should be asked: if you can do so much to base your online operations for $ 0.00- $ 0.05 a day, why not? This is available for almost any budget and goes a long way to protecting you by taking power away from higher authorities and giving it back to ordinary people.
The highest cost for most people is probably not the actual cost of email, but switching from the current account to the new one. I’d say it’s more than worth the time investment. Even if it takes you 10 or 20 hours to switch your accounts and contacts to a new email address, you will now have a reliable emai that can be accessed for years and decades to come. It will pay you dividends in ways you can’t even imagine. And they will grow over time, and privacy around the world continues, and will weaken.
The sooner you switch, the better off you’ll be, and the happier you’ll end up. In addition, the earlier you make the transition, the less work you will need to eventually switch to it in the long run.
What to look for in email providers

There are many problems that email providers can solve, and we will try to explain this as simply as possible. Choose them according to the following criteria:
- Encrypts account data and simplifies and simplifies end-to-end encryption.
- Protects the user’s IP address and does not require any personal information about the user to register.
- Accepts payments in Bitcoin / cryptocurrency.
- Uses a range of industry best security practices that go even beyond what is discussed here.
- Dear, long-standing companies with a good reputation for privacy and honest marketing practices in the community.
This list covers most of what is important.
If you really want to be able to trust your provider, then its ethical reputation, as well as its use of advanced security practices and open source protocols, will help you ensure that everything is up to par.
Meanwhile, you also need to make sure that everything is “kosher” on your part, which may include financial privacy, such as the ability to pay in crypt. By paying in cryptocurrencies, you can help reduce the “parasitic” cycle created by payment processing companies and other similar organizations that track all your financial movements. Finally, you need to make sure that the offer has a good reputation.
Recommended email services for privacy
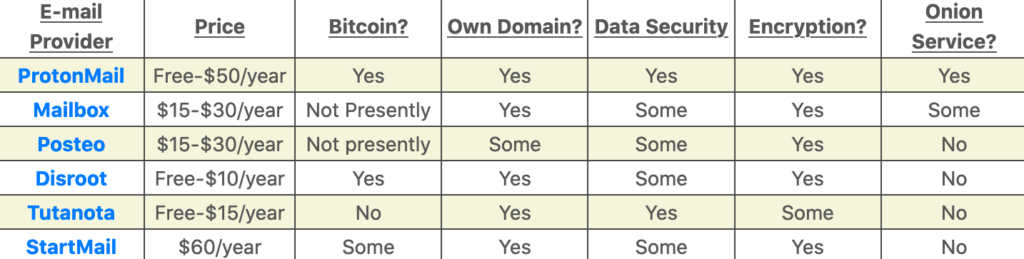
We have compiled a short list of some of the best email providers that have many built-in privacy features and a note of what these services currently offer, as of October 2020. This checklist is not exhaustive, and intentionally omits many of the data related to all of these websites to make it easier for you.
Knowing this, when you select an email, use the table as a very rough guide for choosing. Make sure that you are comfortable with the domain name, as you may have to publish this name several times, since you often have to specify an email address (unless, of course, you are using your own domain).
Second, review each website to see if they are compatible with your needs in terms of direct services or a user interface that is convenient for you. Each site can access different users. Keep in mind that while some sites may offer various services that others do not, all of these websites are of extremely high quality and are a significant step forward compared to using Gmail or any other such mega-provider.
What’s next?

If you have received a new free or paid account, congratulations! Your next step is to start using this account to its full potential as soon as possible, and opt out of your current and supposedly bad provider. You may want to figure out all your other accounts for your programs and apps for a while, which is easier to do if you have a password Manager (which will be covered in the next part), and start migrating everything from your former account to your new email account.
Second, you need to tell all your old email contacts in your address book that you are switching to a different email address. You can also temporarily activate email forwarding from the old address to the new one for the following months, so that you don’t lose anything important.
Soon enough, you’ll find that your old email is turning to dust. At this point, you will want to save all your emails (if necessary) and delete all your old emails and completely deactivate your account to start getting rid of the all-seeing eye of the megacorporation.
Third, if you have really sensitive data, take matters into your own hands and use OpenPGP or other similar protocols that will encrypt your own messages. This way, you don’t need to trust even trusted third parties. Although it is moderately inconvenient, it can offer another tool if you want to increase your personal privacy by using the best services in the first place.
Finally, encourage any like-minded individuals to behave similarly if you are ultimately happy with your new confidential email provider. Such simple steps, such as connecting some relatives and close friends, can have an exponential effect that will have a huge positive impact on society as a whole.
Summarize
It is important for cryptocurrency users to take security and privacy seriously, because it can have disastrous consequences if they are hacked or compromised in any way. Therefore, we give users a serious detailed guide to improve their daily Internet security.
In the second part of the series, we will look at various secure messaging applications, from which you can choose what suits you best. Everyone can have their own niche or specialization that can meet your personal needs. It is often useful to have more than one of these apps for broader purposes.
End of the first part.


